Separate Chaining Hash Table Java
Key delete t x delete x from the list t h x. Unlike link java util map this class uses the convention that values cannot be code null setting the value associated with a key to code null is equivalent to deleting the key from the symbol table.
 Hashing Set 3 Open Addressing Geeksforgeeks
Hashing Set 3 Open Addressing Geeksforgeeks
Implementing our own hash table with separate chaining in java every data structure has its own special characteristics for example a bst is used when quick searching of an element in log n is required.
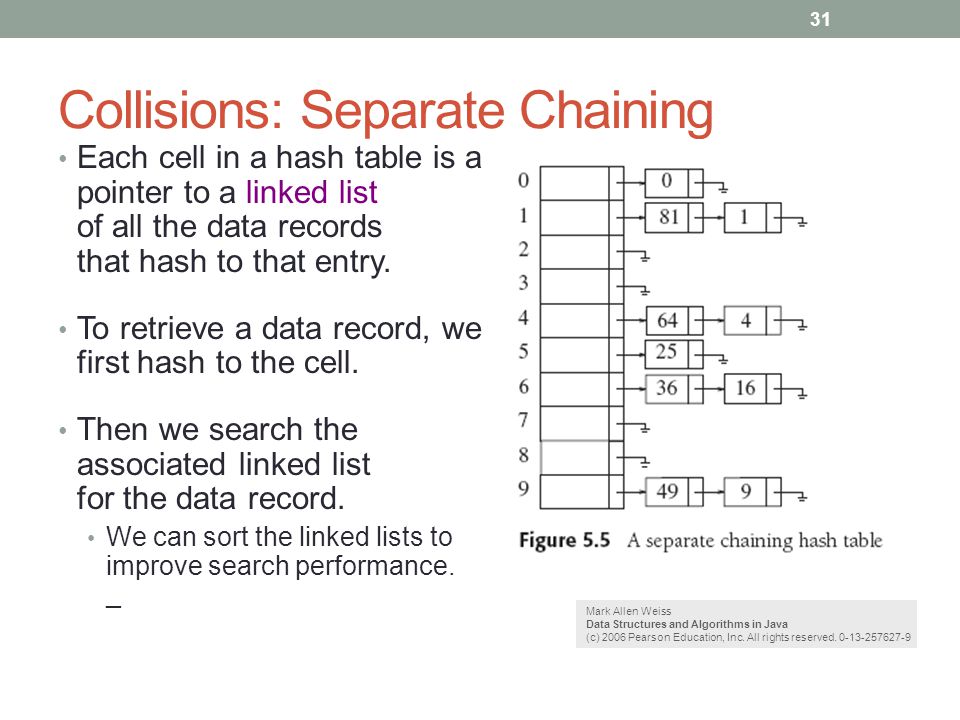
Separate chaining hash table java. See the following pictures separate chaining till insertion of 10 elements after rehashing the hash table got doubled the capacity. Each slot of the array contains a link to a singly linked list containing key value pairs with the same hash. Collision resolution by chaining closed addressing chaining is a possible way to resolve collisions.
Of elements n for each element insertion we ll verify if load factor get increased which means the number of capacity should be increased i e. New key value pairs are added to the end of the list. Lookup algorithm searches through the list to find matching key.
The dictionary operations on a hash table where collision is resolve by chaining is given below search t k search for element with key k in the list t h k insert t x insert x at the head of hte list t h x. Below is an example of how to create a hash table in java using chaining for collision resolution explained below. A heap or a priority queue is used when the minimum or maximum element needs to be fetched in constant time.
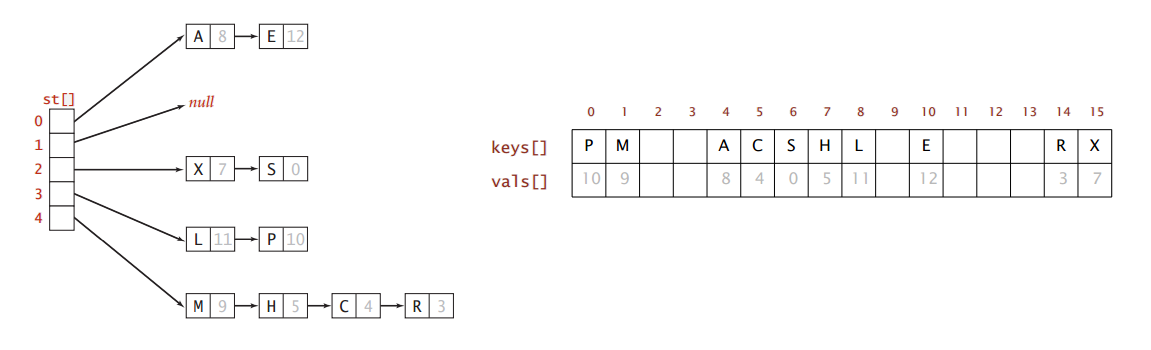
The idea is to make each cell of hash table point to a linked list of records that have same hash function value. Key the worst case running time for insertion is o n 3. It maintains an array of sequentialsearchst objects and implements get and put by computing a hash function to choose which sequentialsearchst can contain the key and then using get and put from sequentialsearchst to complete either job.
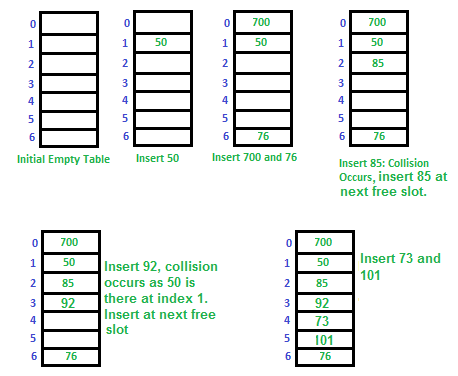
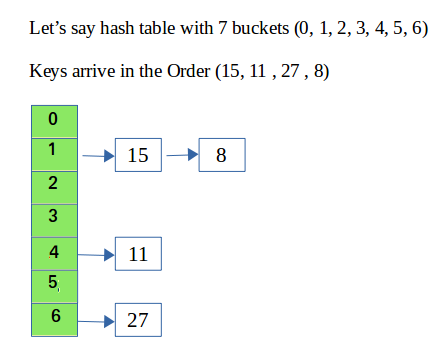
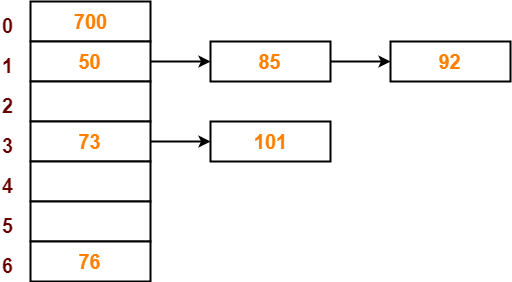
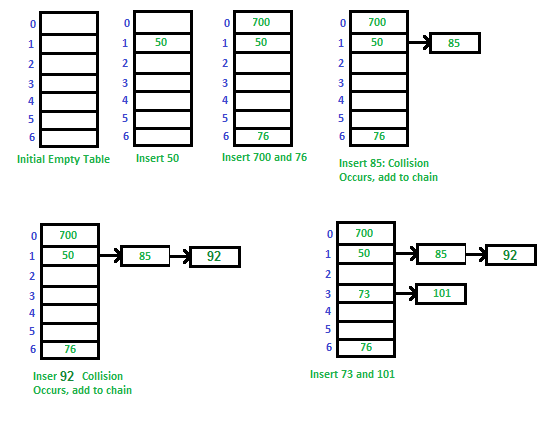
There are a variety of common ways to implement a hash table but the basic parts of any hash table are the array the hash function and handling collisions. The basic methods include get put and delete. Let us consider a simple hash function as key mod 7 and sequence of keys as 50 700 76 85 92 73 101.
P this implementation uses a separate chaining hash table. Capacity of hash table m load factor no. Program separatechaininghashst java implements a symbol table with a separate chaining hash table.
 Lecture Objectives To Learn About Hash Coding And Its Use To
Lecture Objectives To Learn About Hash Coding And Its Use To
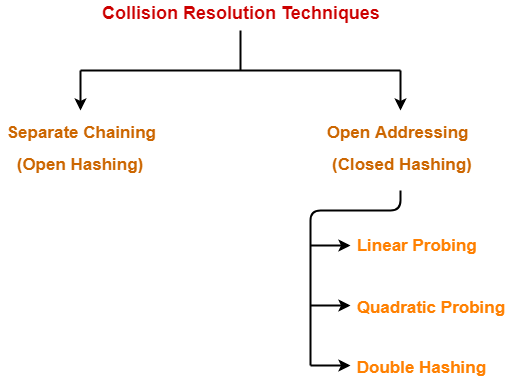
 Separate Chaining Collision Resolution Techniques Gate Vidyalay
Separate Chaining Collision Resolution Techniques Gate Vidyalay
 C Program For Hashing With Chaining Geeksforgeeks
C Program For Hashing With Chaining Geeksforgeeks
 Separate Chaining Hashing Collision Handling Technique
Separate Chaining Hashing Collision Handling Technique
 Separate Chaining Concept Advantages Disadvantages Video
Separate Chaining Concept Advantages Disadvantages Video
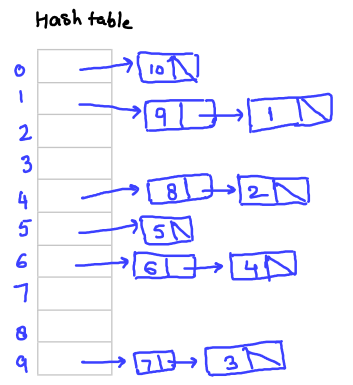 Separate Chaining Hashing Collision Handling Technique
Separate Chaining Hashing Collision Handling Technique
Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcs94iki40bqar Asld2ruybtz56qgrde2o6pn2e89jub0wpwgc6 Usqp Cau
 Hash Table Separate Chaining Source Code Youtube
Hash Table Separate Chaining Source Code Youtube
 Program To Implement Separate Chaining In C Stl Without The Use
Program To Implement Separate Chaining In C Stl Without The Use
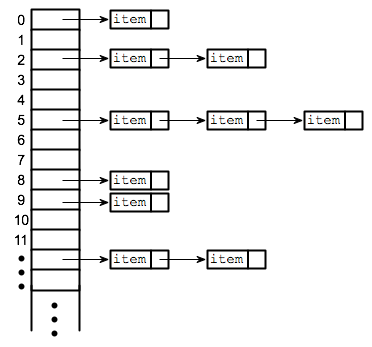 Basics Of Hash Tables Tutorials Notes Data Structures
Basics Of Hash Tables Tutorials Notes Data Structures
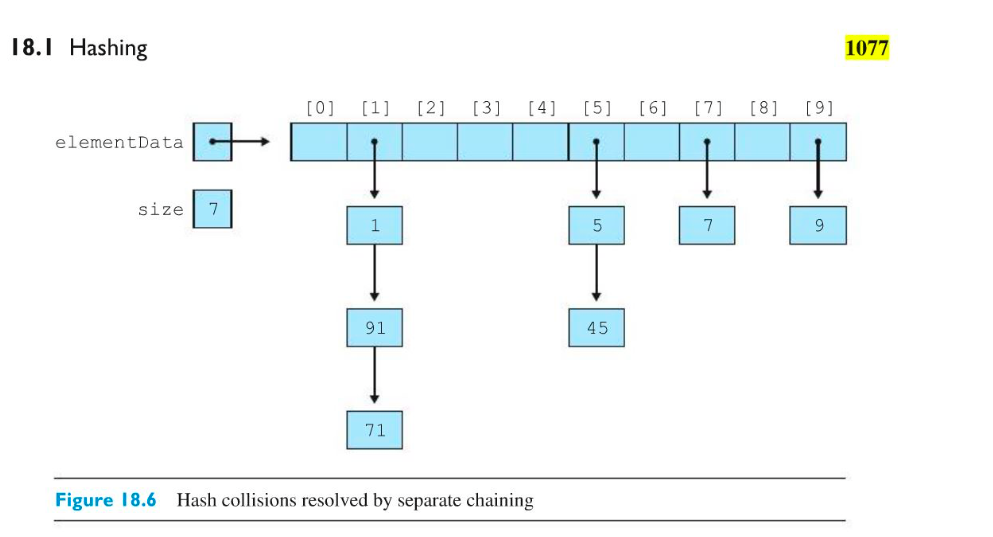 Solved Write A Method Or More In Provided Hashset Java
Solved Write A Method Or More In Provided Hashset Java
 Hash Table In C Programs To Implement Hash Table And Hash Maps
Hash Table In C Programs To Implement Hash Table And Hash Maps
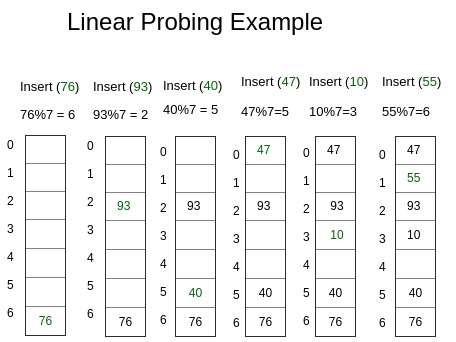 Implementing Own Hash Table With Open Addressing Linear Probing In
Implementing Own Hash Table With Open Addressing Linear Probing In
 Hashing Set 2 Separate Chaining Geeksforgeeks
Hashing Set 2 Separate Chaining Geeksforgeeks
 Solved Hashtable With Java Seperate Chaining With Linked
Solved Hashtable With Java Seperate Chaining With Linked
 Separate Chaining Collision Resolution Techniques Gate Vidyalay
Separate Chaining Collision Resolution Techniques Gate Vidyalay
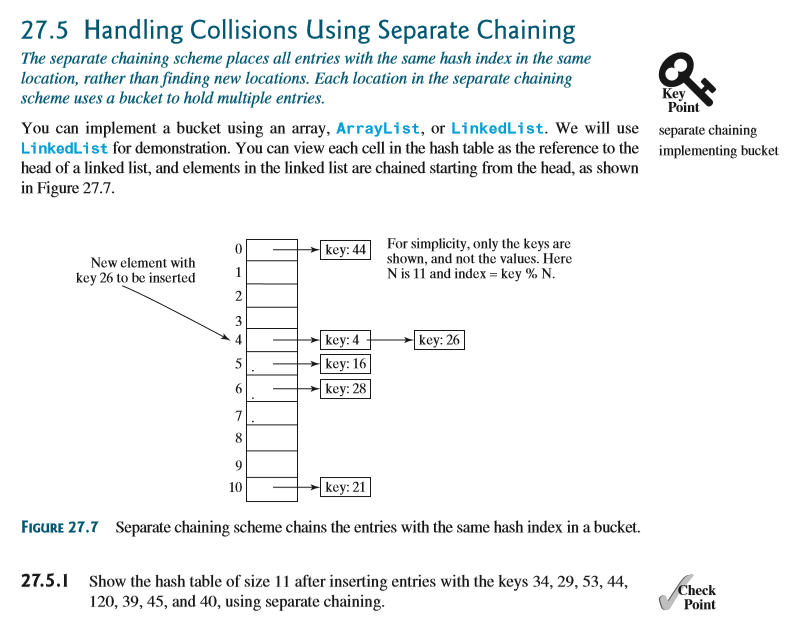 Language Java Introduction In Chapter 27 We Learne Chegg Com
Language Java Introduction In Chapter 27 We Learne Chegg Com
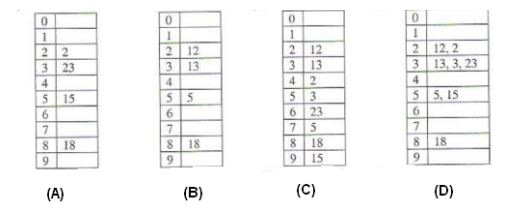 Practice Problems On Hashing Geeksforgeeks
Practice Problems On Hashing Geeksforgeeks
 Hash Tables Tutorial C C Java Bits And Pieces Of Code
Hash Tables Tutorial C C Java Bits And Pieces Of Code
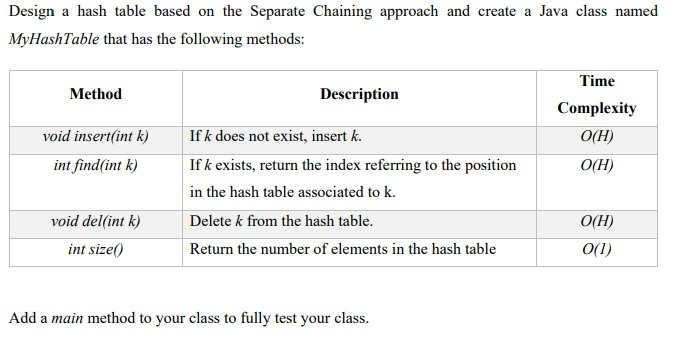 Solved Design A Hash Table Based On The Separate Chaining
Solved Design A Hash Table Based On The Separate Chaining
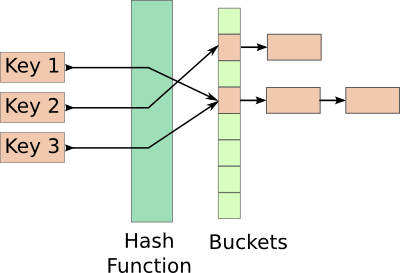 Hash Tables Tutorial C C Java Bits And Pieces Of Code
Hash Tables Tutorial C C Java Bits And Pieces Of Code
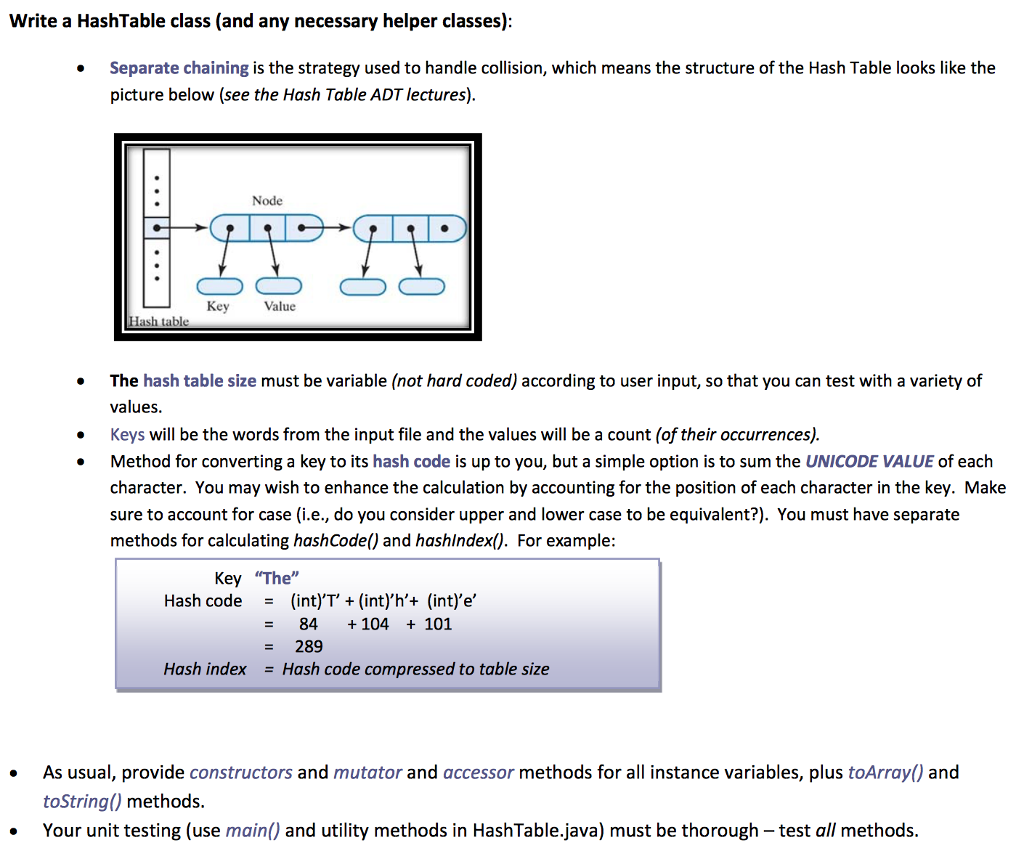 Solved Write A Hashtable Class And Any Necessary Helper
Solved Write A Hashtable Class And Any Necessary Helper
 Implementing Our Own Hash Table With Separate Chaining In Java
Implementing Our Own Hash Table With Separate Chaining In Java
Hash Table Chaining Java C Algorithms And Data Structures
 Separate Chaining Concept Advantages Disadvantages Video
Separate Chaining Concept Advantages Disadvantages Video
Buttercola Data Structure Algorithms Hash Tables
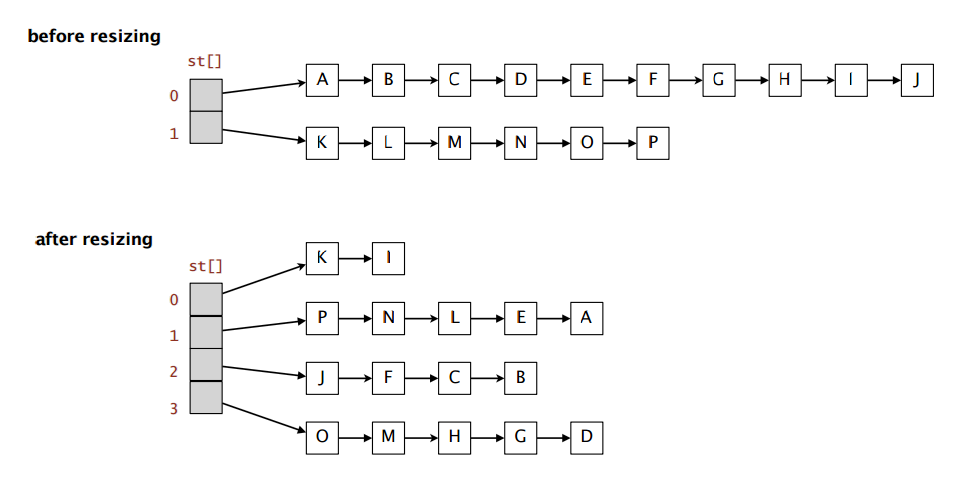 Hash Tables Sounds Familiar But We Re Going To By Omar
Hash Tables Sounds Familiar But We Re Going To By Omar
Hash Table Open Addressing Strategy Java C Algorithms
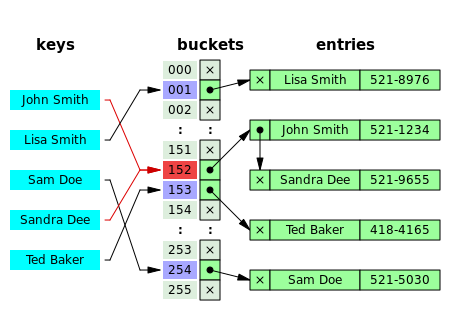
 Hash Tables Sounds Familiar But We Re Going To By Omar
Hash Tables Sounds Familiar But We Re Going To By Omar

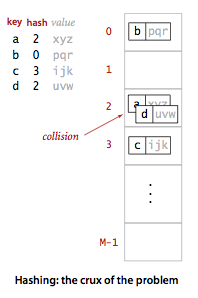





Posting Komentar
Posting Komentar