What Are The Three Types Of Authentication
Authentication is the first step in access control and there are three common factors used for authentication. Types of user authentication.
 Protection And Security Ppt Video Online Download
Protection And Security Ppt Video Online Download
This information is called an authentication factor and there are three types.
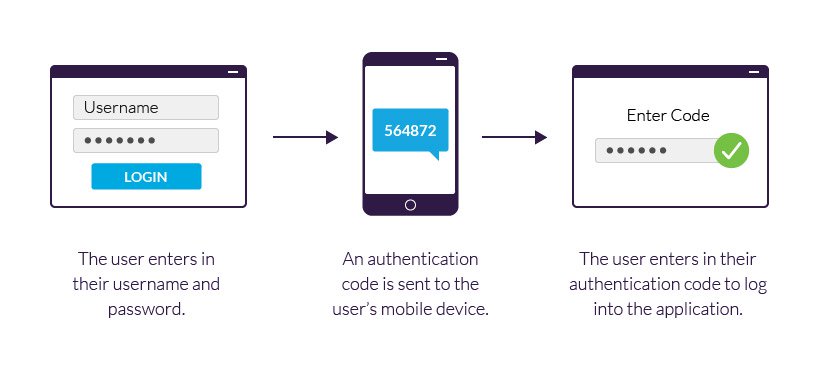
What are the three types of authentication. These are called biometrics and there are many types of it. The type three authentication is something we are which are physical characteristics that we or our body has specifically. Multi factor authentication is preferred as it is much more difficult for an intruder to overcome.
What are the types of authentication. In this approach a unique generated value is assigned to each first time user signifying that the user is known. As far as authentication is concerned there are mainly three types of wlan authentication methods that are used today.
Three factor authentication 3fa is the use of identity confirming credentials from three separate categories of authentication factors typically the knowledge possession and inherence. The gif above is an example of how biometrics can be used for authentication. This article provides you with good understanding of the three factors of authentication and how they can be used together with multifactor authentication.
Authentication can be considered to be of three types. Api keys were created as somewhat of a fix to the early authentication issues of http basic authentication and other such systems. Authentication is an additional step that verifies the person entering a username is in fact the owner of that username.
Something you know something you have and something you are. This factor might not be as known as the ones already mentioned. When the user attempts to re enter the system their unique key sometimes generated from their hardware combination and ip data and other times.
In art antiques and anthropology a common problem is verifying that a given artifact was produced by a certain person or in a certain place or period of history in computer science verifying a user s identity is often required to allow access to confidential data or systems. Once a user has been authenticated it s safe to allow them access to the network. Here s where secure authentication methods come in.
Authentication is relevant to multiple fields. With just a password an attacker only has to have a single attack skill and wage a single successful attack to impersonate the victim. In order for a user to confirm their identity the individual must provide a piece of information that only the user and the server knows.
For example these can be fingerprints retina scans iris scans facial scans palm scans hand geometry voice recognition handwriting or keyboard dynamics. By combining two or three factors from these three categories a multi factor authentication is crafted. Factors the user must know in order to log in are considered a knowledge.
 3 Common Methods Of Api Authentication Explained Nordic Apis
3 Common Methods Of Api Authentication Explained Nordic Apis
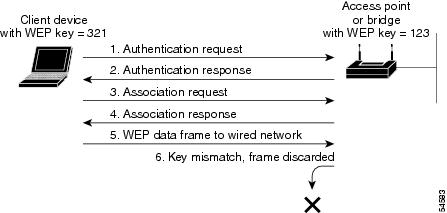 Authentication Types For Wireless Devices Cisco
Authentication Types For Wireless Devices Cisco
 Authentication Type An Overview Sciencedirect Topics
Authentication Type An Overview Sciencedirect Topics
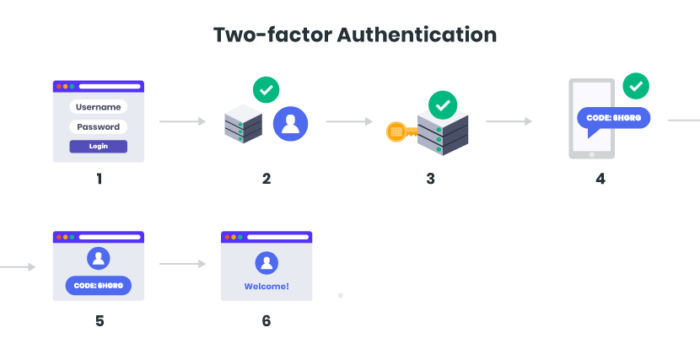 Understanding User Authentication 3 Basics You Should Know
Understanding User Authentication 3 Basics You Should Know
 Solved Quiz 2 Authentication Web And Network Name Ne
Solved Quiz 2 Authentication Web And Network Name Ne
 Solved Assignment Authentication And Account Management
Solved Assignment Authentication And Account Management
 What Is Multi Factor Authentication Process Management Flovate
What Is Multi Factor Authentication Process Management Flovate

 A Summary Of Three Major Types Of Authentication Methods
A Summary Of Three Major Types Of Authentication Methods
 Authentication Factor An Overview Sciencedirect Topics
Authentication Factor An Overview Sciencedirect Topics
 Understanding User Authentication 3 Basics You Should Know
Understanding User Authentication 3 Basics You Should Know
 Can Multi Factor Authentication Help Healthcare S Security Posture
Can Multi Factor Authentication Help Healthcare S Security Posture
 A Summary Of Three Major Types Of Authentication Methods
A Summary Of Three Major Types Of Authentication Methods
 Types Of Authentication Methods Optimal Idm
Types Of Authentication Methods Optimal Idm
 What Is Two Factor Authentication Pros And Cons Of 2fa Imperva
What Is Two Factor Authentication Pros And Cons Of 2fa Imperva
 Three Types Of Authentication Download Scientific Diagram
Three Types Of Authentication Download Scientific Diagram

 Common Types Of Two Factor Authentication Private Tunnel
Common Types Of Two Factor Authentication Private Tunnel
Authentication Types In Api Manager
Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcqu Ajvnbczi7lksj4pe P Om0oog Vi Q15qsslhkhkgr6zgb Usqp Cau
 Understanding Network Authentication Methods Solarwinds Msp
Understanding Network Authentication Methods Solarwinds Msp
 Multi Factor Authentication Mfa What Is It And Why Do You Need
Multi Factor Authentication Mfa What Is It And Why Do You Need
 Solved The Three Types Of Authentication Are Something Yo
Solved The Three Types Of Authentication Are Something Yo
Core Vidm Components Enable Flexible Authentication Methods

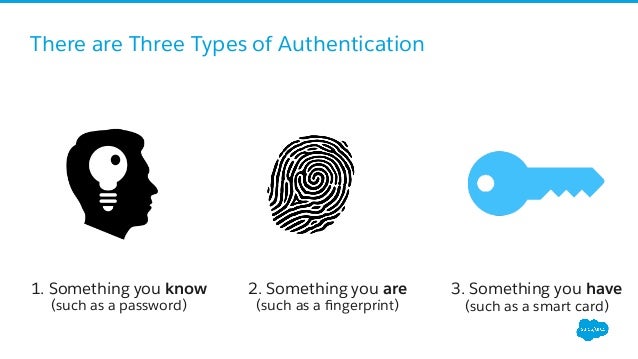 Secure Your Salesforce Org With Two Factor Authentication
Secure Your Salesforce Org With Two Factor Authentication

Multi Factor Authentication What It Is And Why Small Businesses
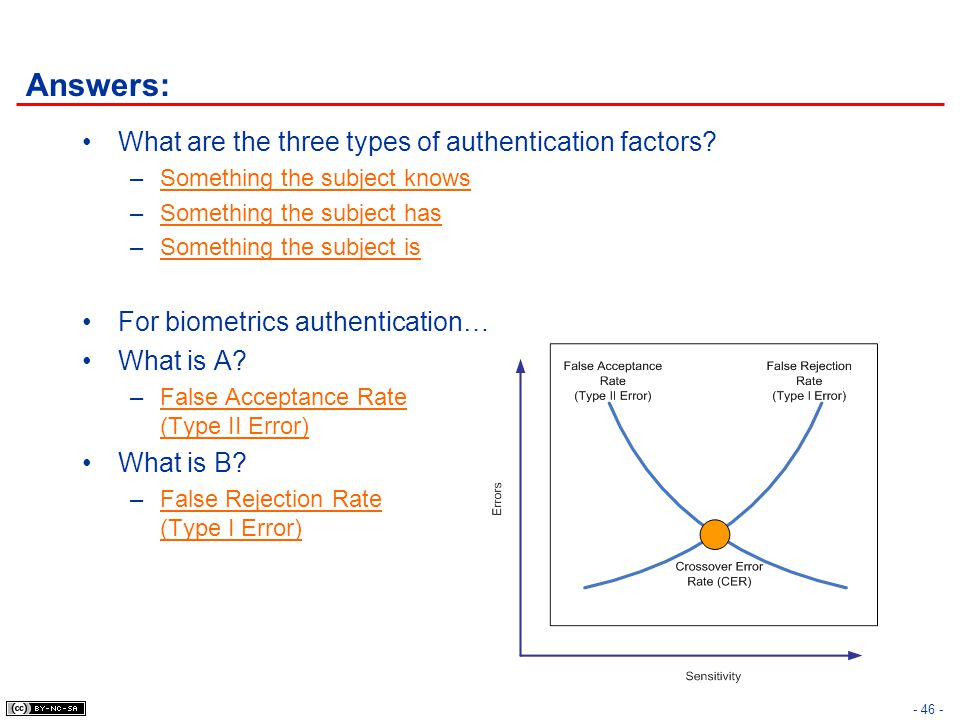 Cissp Common Body Of Knowledge Review Access Control Domain
Cissp Common Body Of Knowledge Review Access Control Domain
 Web Authentication Methods Explained Risingstack
Web Authentication Methods Explained Risingstack
 Prog Advanced Web Applications With Net Prog Advanced Web
Prog Advanced Web Applications With Net Prog Advanced Web
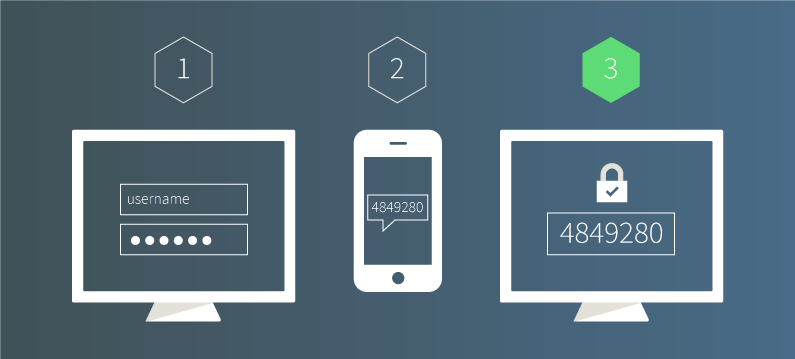 The 5 Factors Of Authentication Nowadays The Terms Multi Factor
The 5 Factors Of Authentication Nowadays The Terms Multi Factor
 Back To Basics Multi Factor Authentication Mfa Nist
Back To Basics Multi Factor Authentication Mfa Nist






Posting Komentar
Posting Komentar